A quick note: In the time since I first wrote this piece, some of this material has been covered by other authors. Repetition is key to absorbing information, so here it is again.
A Brief Primer on IP Networking
IP (Internet Protocol) networking is, safe to say, the most prevalent form of data networking on Earth. It’s what makes the Internet work1. It was certainly not the first form of data networking, and it’s not the only form today, but it has spread into pretty much every corner. My goal today is to provide an overview of how IP networking works, because I believe it will help with understanding some of the topics that will come up when I actually get around to talking about email.
Stacked
Any data networking scheme, Internet or otherwise, is made of up a number of elements that work together to transfer data from hither to yon. The combination of elements is usually described as a “stack.” A given element in the stack accepts data from the element above it, performs some operation that furthers the goal of transmitting the data, and passes it off to the element below it2. Elements that are closer to the user are typically described as at the top of the stack. Elements that are closer to the physical wire are at the bottom.
A layer in the stack at one end “talks to” its counterpart layer at the other end. Each layer doesn’t really know, or care, what other layers are doing. Layer 4 (for example) doesn’t care how layers 1-3 work, as long as they are getting the job done of enabling communication with Layer 4 at the other end.
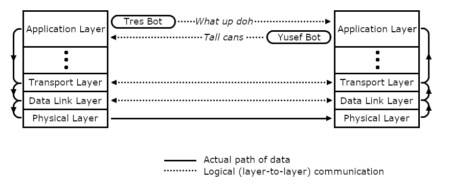
Those funny Europeans have a designed-by-committee model that divides networking into seven distinct layers3. Here in ‘Murica, it’s more like four-ish layers.
Protocols
The set of rules for polite and correct communication at any layer is called a protocol. These function very much like protocols in interpersonal communications. Some things are appropriate to say, some inappropriate but tolerated, and some forbidden. IT is chock full to the gills with protocols. Pretty much any acronym you see that ends in “P” refers to a protocol4. I’ve already mentioned one: Internet Protocol. All of these protocols are described in excruciating detail5 in documents misleadingly called “Requests For Comments” (RFCs). I won’t discuss those here.
Physical / Data Link Layers
I’m not going to talk about these bottom-most layers, except to say that the data link protocol most people have heard of is Ethernet, using either twisted pair cabling6 or radio (“Wi-fi”) as the “physical” medium.
Network Layer (IP)
IP sits on top of the data link layer and its primary job is getting data from one computer to another computer. Computers are identified by an “IP address,” examples of which most of you surely have seen. It’s four numbers, between 0 and 255, separated by periods, like so: 192.168.0.1317. This nominally allows for 232 (2 to the 32nd power, ~4 billion) unique addresses, but for various reasons, the actual number of usable addresses is much lower. A significant feature of IP addresses is that they are “routable.” That is, kind of like a telephone number, you can look at the first part of the address, and say generally where a device with that address must be located8. Network devices, strangely called “routers,” move data across the Internet. Central routers have only a general idea where a device with a specific IP address might be (“over there, somewhere”), but as data moves closer to the device, the routers have more detailed information about exactly where that device is.
Transport Layer (TCP and UDP)
The Transport Layer sits above IP, and its job is to provide the infrastructure for specific applications to communicate. In IP networks, there are primarily two protocols that operate at this layer: Transmission Control Protocol (TCP) and User Datagram Protocol (UDP).
TCP is a “reliable, connection-oriented” protocol. It’s like a phone call: when you attempt to establish a connection, you can tell when the connection is made, and when it ends, and you can tell when the data has been garbled. UDP, in contrast, is an “unreliable, datagram oriented” protocol. It’s like US Postal Mail: you put an address on a letter and drop it in the box, and usually it gets to the destination in predictable time, but sometimes it takes longer, and occasionally it is lost altogether.
On any computer, there will be multiple applications that need to communicate over the network. They all have to share the same IP address, so there needs to be a way to identify which network data goes to which application. TCP and UDP both use numbered “ports” for this purpose. The combination of IP address and port number (and protocol, TCP or UDP) uniquely identifies any application running on an Internet-connected computer. Port numbers run from 1 to ~65000, and each application on a computer uses a distinct port. Which port an application uses depends on the role of the application.
An application that provides a service, something that other applications or users will come looking for, is called a “server,”9 like a “web server,” “mail server”, etc. Applications that consume those services, like web browsers or email readers, etc., are called “clients.” When a client wants to establish a new connection to a server, the client needs both the IP address and the port number of the server. IP address can be looked up based on the name of the computer, but servers almost always use “well known,” port numbers, according to the application. Web servers use port 80, mail servers use port 2510, etc. In this way, the client knows the server port number based on what kind of client it is. The client tells the server about its own IP address and port number as part of the connection request, so the port that the client uses is usually unimportant, and typically clients use random-ish port numbers in the 20,000 – 30,000 range.
Application Layer (So many protocols)
This top-most layer is where applications that users actually care about operate: web, email, print, file and directory services, etc. But, for the purposes of this article, the protocols used by the specific applications aren’t important. There are a number of application layer protocols that are specific to email, but I’ll talk about those in a later article.
The Key Learning
After all that, what I really want readers to take away11 is the concept of TCP and UDP port numbers, and that specific application-layer protocols use specific ports, and only those ports. For any protocol, there may be lots of different programs that implement that protocol, but they always use the same ports.
Next installment, I’ll talk about some of the groundwork that needs to be done before you can host an internet connected email service.
1 You can tell because it’s right there in the name.
2 Or the other way ‘round, at the other end.
3 The ISO seven-layer salad. One of the few things I actually remember from Data Networks class, thanks to a juvenile but effective mnemonic devised by my roommate.
4 Just like any acronym that starts with “S” usually means “simple”. Spoiler alert: simple is relative.
5 And yet some people still fuck up protocol implementation. Sometimes accidentally, sometimes not. See also, Microsoft.
6 These days, “Category 5” or “Category 6” cabling is optimized for high-speed Ethernet, but Ethernet over twisted pair was created to run over crappy telephone wiring already present in commercial buildings.
7 This is an IP version 4 (IPv4) address. There is a version 6 of IP (IPv6), which uses longer addresses, to allow for more unique devices in the world.
8 Well, not as much like a phone number since number portability fucked everything up.
9 No to be confused with a rack-mount data center type computer. This is why I avoided that word in Part 2.
10 And other port numbers, too, depending on circumstances, but these are the basic ports. Peruse a complete list here: https://en.wikipedia.org/wiki/List_of_TCP_and_UDP_port_numbers.
11 Like a hunk of batter fried cod wrapped in greasy newspaper.

Thanks for writing 🙂
Now would seem to be a pretty apt time for this…
The lecture on footnotes?
Ackshually, footnotes are part of AP style, which was taken over by communist a-holes. So when you use footnote’s you are supporting marxism.
Ha!
I keed. I don’t know who the f*ck took over AP.
But it probably was communists.
Based on their recent output, I can’t disagree.
In a more… specific way, the AP style was over taken* by the MLA style. Which outright sucks.
*see what I did, huh? Flipped it around…
👀
Dude. It was clearly aliens.
Communist Mutants from Outer Space!
https://m.youtube.com/watch?v=8gIjQGKR9As
Ha!
You can tell those sneaky little bastards are dirty commies. They’re pooping on everything.
I did cross my mind.
It*
grumble grumble
Did you dog your thoughts, too?
Legit LOL.
Thanks for the submission. I learned a bit and confirmed a bit.
Thanks Grumman. Finally I sort of learned a little, which I’ll promptly forget.
in documents misleadingly called “Requests For Comments” (RFCs)
Heh.
They also double as cures for insomnia.
RFC 1149 is appropriate here.
RIP Jon Postel.
ARPAWOCKY
The Doom that came to Puppet
You should write stereo instructions. Much more enjoyable than most tech stuff I’ve read. Thx.
My 20 year rice cooker croaked and I finally bought a one of the computer controlled ones – a Zojirushi.
The English instructions were a wonderful throwback of stilted Japanese to English translation that doesn’t really happen much anymore. It’s rather different than the usual machine translated Chinese to English on most electronics and the like today.
❤️❤️
https://mobile.twitter.com/MaxineVVaters/status/1600635406927675392
That is almost “Guam tip over” level commentary.
She really is one of a kind, except for all the others. It’s a problem with democracy.
“demonifying”
Sure, we laugh but when Webster’s incorporates this in the dictionary next year Miss Waters will be laughing at us. She’s cutting edge.
She’s on some edge, that’s for sure.
I saw that too. Jeebus H Christ.
lol
Maxine’s favorite band?
Lol. Outside of you all and known fuckery when I mention my wife’s grooming business…no one ever. What a cunte
I really really really need to do this.
So, yeah…I ordered some ammo today. 😛
“Biden Quotes Scripture, Vows to ‘Limit the Number of Bullets That Can Be in a Cartridge’”
Maxine has company
“high-capacity ammunition”
Where’s my shocked face? 🧐
Someone check on Tonio. He must be stroking out.
/not euphamism
Pisces: Ace of Swords – Triumph, the excessive degree in everything, great force, in love as well as in hatred.
I’m as pretty as Kelly Loeffler! – Herschel Walker
Thanks for this, Grummun. Between this and Pat’s articles, I got a lot of learnin’ to do. Not a lot of time for it now, so these are all getting bookmarked into a “one of these days” folder.
I really need to take Pat’s articles to heart and put some time into hardening the home network: install Pi-Hole, replace vanilla Firefox with something more security conscious, etc.
Me too.
Thanks for the kind words, folks. I’m for bed.
Thanks Grummun! I missed you ‘cause I was zooming.
Looking forward to the rest of the series. I set up an email server for myself and a couple of friends back in high school just to screw around with, but that was a long time ago. It had no security features or even spam filtering. I’ve been considering self-hosting my email for quite a while, but it seems like configurationing everything such that your mail doesn’t get automatically spam filtered by Google seems to be the most difficult part. Even my paid email service was trapped in the Google spam net for a while.
Also, my privacy schizo articles now seem extremely deficient in detail.
Tresbot and Yusefbot literally made me laugh out loud.
It’s the artisanal, finely crafted details that bring me joy.
#metoo
Same-same.
Now I want to write both of those.
I’m gladdened that Glibs will live on in the next plane of existence.
This all seems suspiciously like something I’m normally paid to deal with.
We start talking SPF, DMARC and DKIM, I’ll know you’re secretly a coworker.
(But, seriously, thanks for the write-up – I didn’t even have an “aktually” moment).
I think that what is needed to turn the tide against the seconders in the coming war, and to prepare the world for The First That Shall Change Everything, is a First before any seconder even existed. I need to access a place in the FIrstiverse so remote, so far back and removed from everything that only The Great Firster has hitherto had any knowledge of it.
I need to First where no Firster has Firsted before.
Also, fuck MikeS.
Well, I am a place where no Firster has Firsted before.
You two should just get a room already.
Not that I would ever lower myself to touch MikeS, but it should be known that Firster’s never get intimate anywhere where they are surrounded by four walls and a roof, or what you seconders would call a room. This is completely against the culture of Firsting. It breaks The Code Of The First.
I could write a whole book on the finer details on the copulations and mating rituals of Firsters.
My Day At The Zoo by Brochettaward
What sort of foul seconding being would compare Firsters, the greatest of all of the creations of The Great Firster, to wild animals?
I am a product of The Great Firster’s First Seed. This is low, even for you.
It’s gonna be a while until the First of May
I don’t understand most of this but this seems related.
https://youtu.be/XrhoIzQr6vI
Morning Glibs.
https://www.wfmz.com/news/area/western-newjersey/liberty-villages-last-holiday-shopping-season-a-look-at-the-past-and-future-of-the/article_fdddcc3c-767e-11ed-b336-6701b527ad33.html
A teenaged me used to work there. 😒
There it is.
https://www.wtae.com/article/two-pitt-students-charged-with-abuse-of-a-corpse/42131168
“Probably” Trump supporters. /MSM
“ Different witnesses told police that student Amay Gupta made mocking sexual comments about a male cadaver while having his hand inside the body’s chest.”
This is a crime?
Read some of the student interview quotes and weep for the English language and the state of education that these people made it into college.
https://ktla.com/news/rapper-who-bragged-about-committing-covid-19-fraud-in-music-video-sentenced-to-federal-prison/
LOL. 😂😂
Dang
$700,000 in three months? That’s a hell of an unemployment benefit.
suh’ fam
whats goody
https://nypost.com/2022/12/07/former-nazi-secretary-97-says-she-is-sorry/
Nazi’s everywhere!
Oh wait, this is a real one…
Let this be a warning to future generations.
Mornin’ all. Up early so I can get the gym done early and be ready for an interview today.
The Sun might even come out here in southern NH.
Mornin’, reprobates.
Not sure why I am awake, but will resume sleeping shortly.
Mrs. Patzer, the eldest spawn, and yours truly are all laid up with the ‘vid since Sunday. Sort of like a bad cold that refuses to go away, and I am perpetually exhausted. It’s good to see that the world is still completely absurd and there are a few people who understand this.
Zinc, Quercetin, and a fat rail of crystal meth should get ya going.
Feel better.
Good morning, ‘patzie (so sorry you and yours are ailing! Get better quicker!) Sean, DEG (good luck with the interview!) homey, Stinky, and ‘bodru!
A virtual Friday for me, as I’m taking tomorrow off for my sister’s lunchtime retirement party across town from both my home and my office. Today’s also a water aerobics day for me, so…yay!
Speaking of Da ‘VID, the big boss’s wife came down with it, so BB has been WFH all week as a precaution. My boss is WFH today too, so I guess….I’m in charge! 😃
Give everybody 59 min off.
54 min 45 seconds off.
54:40 or fight!
Fight then.
Ok, but at the beginning, in the middle, or at the end of the day?
1 block of 7min 22 seconds each hour.
Ah, the 59-minute rule that like so many other rules doesn’t apply to contractors. Contractors actually have to work.
Now’s your chance to get rid of all those other employees that are a problem. You know, the lazy ones, the ambitious ones, those that are perpetually early (late).
And good morning GT, Patz, DEG, Sean, Mr Cool, Wiz, Robu, UCS just in case, and all the other early birds.
Good morning, 4(20) – and OBE and U!
Morning folks.
Morning.
Good morning.
We know who’s got his coffee. It’s only morning without it.
Morning, whatever… grumble…
Morning!
I run my own servers for a lot of things, but email is not one of them.
Unless you like a lot of headache, outsource it
Illegals Gone Wild
Don’t complain LA. You voted for it.
If the 70s and 80s are any indication, there is long way to go before voters finally get sick of this sort of thing.
A -10 American this morning. Later we’re headed out for a monthly shopping trip to the big box neighborhood. 30 miles, 4 gals of gas round trip, a restaurant meal and back home after dark. Early is different for me and the missus and grocery shopping shouldn’t require an inspection of each head of lettuce in the bin but it does.
I saw A-10 and thought brrrrt instead of brrrr.
Same here